View Vulnerability Details
To view detailed information about a vulnerability, select the View details icon near the needed vulnerability in the Vulnerabilities Table, the Top 10 Unique Vulnerabilities Section, or the table on the Vulnerabilities tab in the host detailed view pop-up window (see View Host Details).
In the pop-up window that appears, you can view:
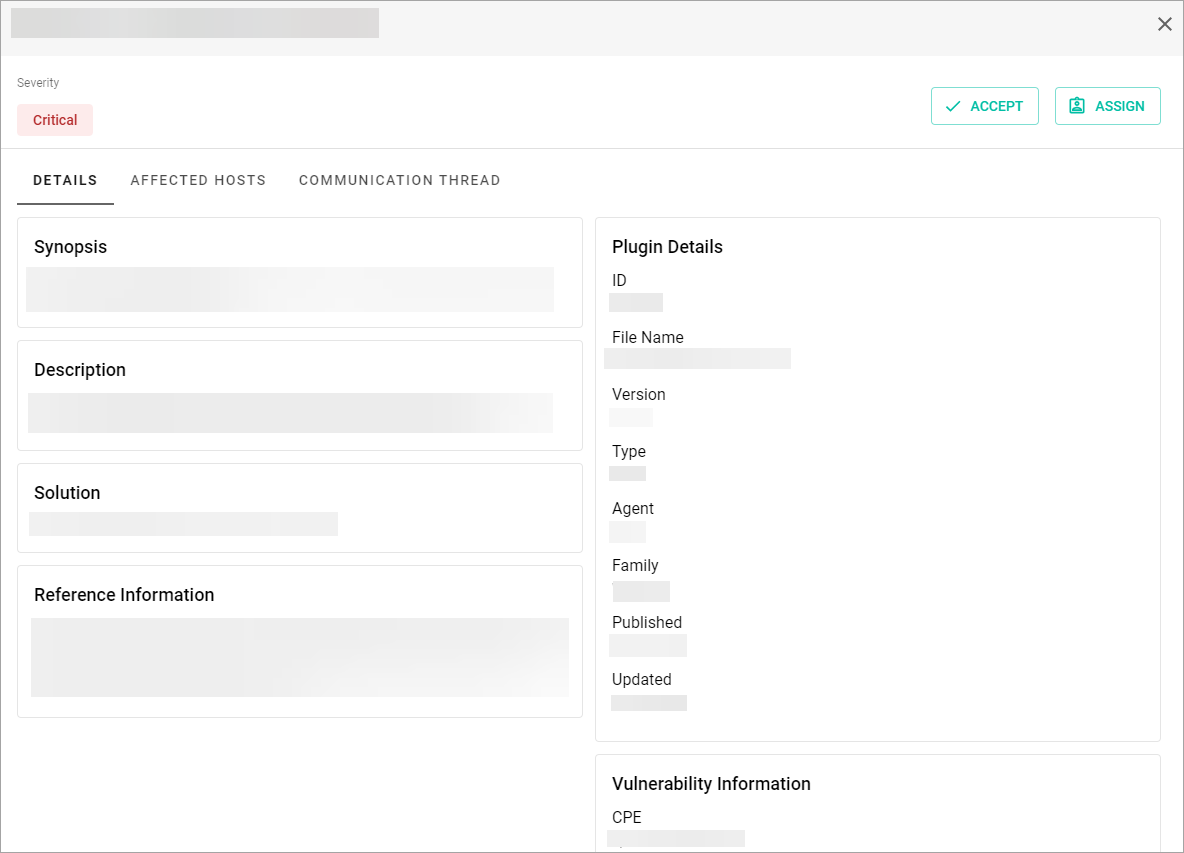
- The window name that corresponds to the plugin name.
- The severity of the vulnerability.
- The user to whom the vulnerability is assigned. If the vulnerability is unassigned, you will see None in the Assigned to section.
- To reassign or unassign the vulnerability, select the Pencil icon in the Assigned to section. For the further steps, see the Assign Vulnerability topic.
- To accept the vulnerability, in the upper-right corner, select the Accept button. In the pop-up window, provide the Acceptance Justification, Response (optional) information. If you turn on the Compensating Control toggle, provide the Compensating Control information and add attachments, if there are any.
- The accepted vulnerability will appear in the Accepted Vulnerabilities table.
- The Assign button if the vulnerability hasn’t been assigned to a user.
- To assign the vulnerability, select the Assign button. For the further steps, see the Assign Vulnerability topic.
- The Details, Affected Hosts, and Communication Thread tabs.
The Details tab consists of the following sections:
- Synopsis
- Description
- Solution
- Reference Information
- Plugin Details
- Vulnerability Information
- Vulnerability Information for this Host (available only in the table on the Vulnerabilities tab in the host detailed view pop-up window (see View Host Details)).
The Affected Hosts tab contains the table where you can:
- Find a host affected by the vulnerability by entering at least three characters of the Host IP, Host Name, or OS Version information in the Search field, and then selecting the Search icon.
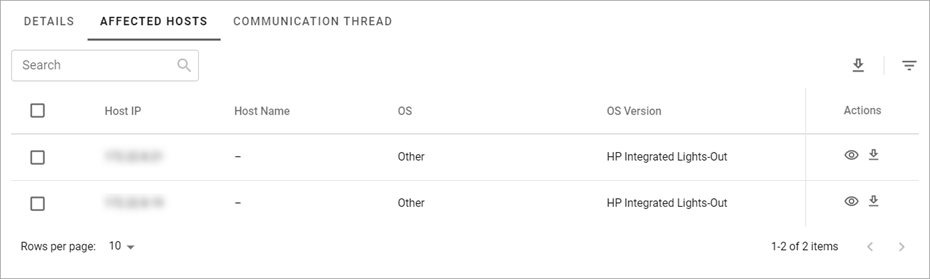
- Download information about all affected hosts by selecting the Download icon in the upper-right corner of the table (see Download Hosts Information).
- Filter the affected hosts list by selecting the Filter icon (see Filter Hosts List).
-
View the list of affected by the vulnerability hosts in the table.
The information in the table is grouped into the following columns:
- Host IP—a unique identification number of a host.
- Host Name—a title of a host.
- OS—an operating system of a host.
- OS Version—a version of an operating system of a host.
- Actions— shows the following icons:
- The View details icon with which you can view the detailed information about a host from the list (see View Host Details).
- The Download icon with which you can download the information about a host from the list (see Download Hosts Information).
On the Communication Thread tab, you can:
- Ask a question about the related vulnerabilities by entering your message in the Type a message field and then selecting the Send icon or press the Enter button. Your message should not exceed 500 characters.
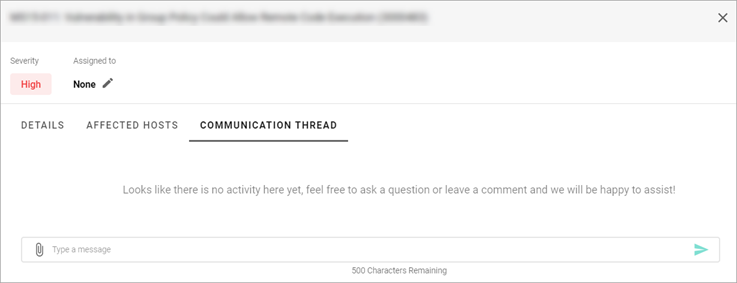
- Attach a file to your message by selecting the Add Attachment icon in the Type a message field and then selecting the needed file from your computer.
- Note: You can add maximum 3 attachments with the .png, .jpg, .jpeg, .mov, .mp4, and .pdf extensions. The maximum file size is 10 MB.
- View the previous messages if there are any.
Related Topics