VTM Page
The Fortified’s Vulnerability Threat Management Program (VTM) allows healthcare organizations to meet or exceed the mandated regulatory requirements to identify and document reasonably anticipated threats to electronic Protected Health Information (ePHI).
For more information about Fortified’s Vulnerability Threat Management Program, please visit the Vulnerability Threat Management (VTM) Program webpage on the Fortified Health Security website.
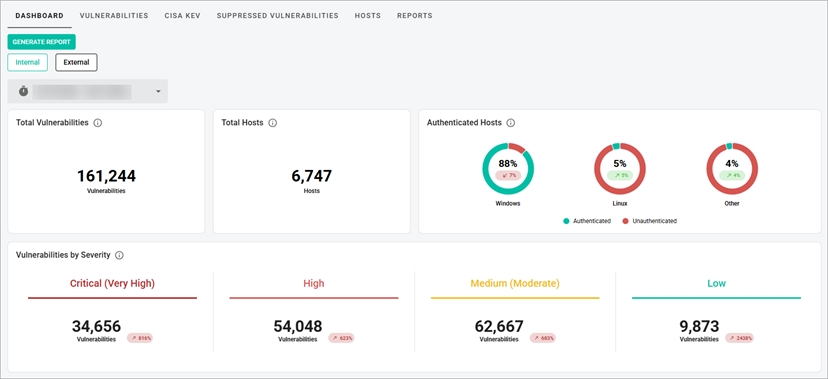
On the VTM page, you can view details and perform actions that help efficiently work with all found vulnerabilities.
Vulnerabilities are instances of a potential security issues found by a plugin.
The VTM page consists of the Dashboard, Vulnerabilities, Suppressed Vulnerabilities, Hosts, and Reports tabs.
- Note: Users with different user roles and permissions may have different view and functionality available (see User Roles and Permissions).
Related Topics
Left-Side Menu (Client Access)
Suppressed Vulnerabilities Tab