Filter Accepted Vulnerabilities List
With filtering, you can customize the vulnerabilities list according to the selected criteria. The Filter icon is located above the upper-right corner of the Accepted Vulnerabilities table.
After the Filter icon is selected, the Filters pop-up window appears.
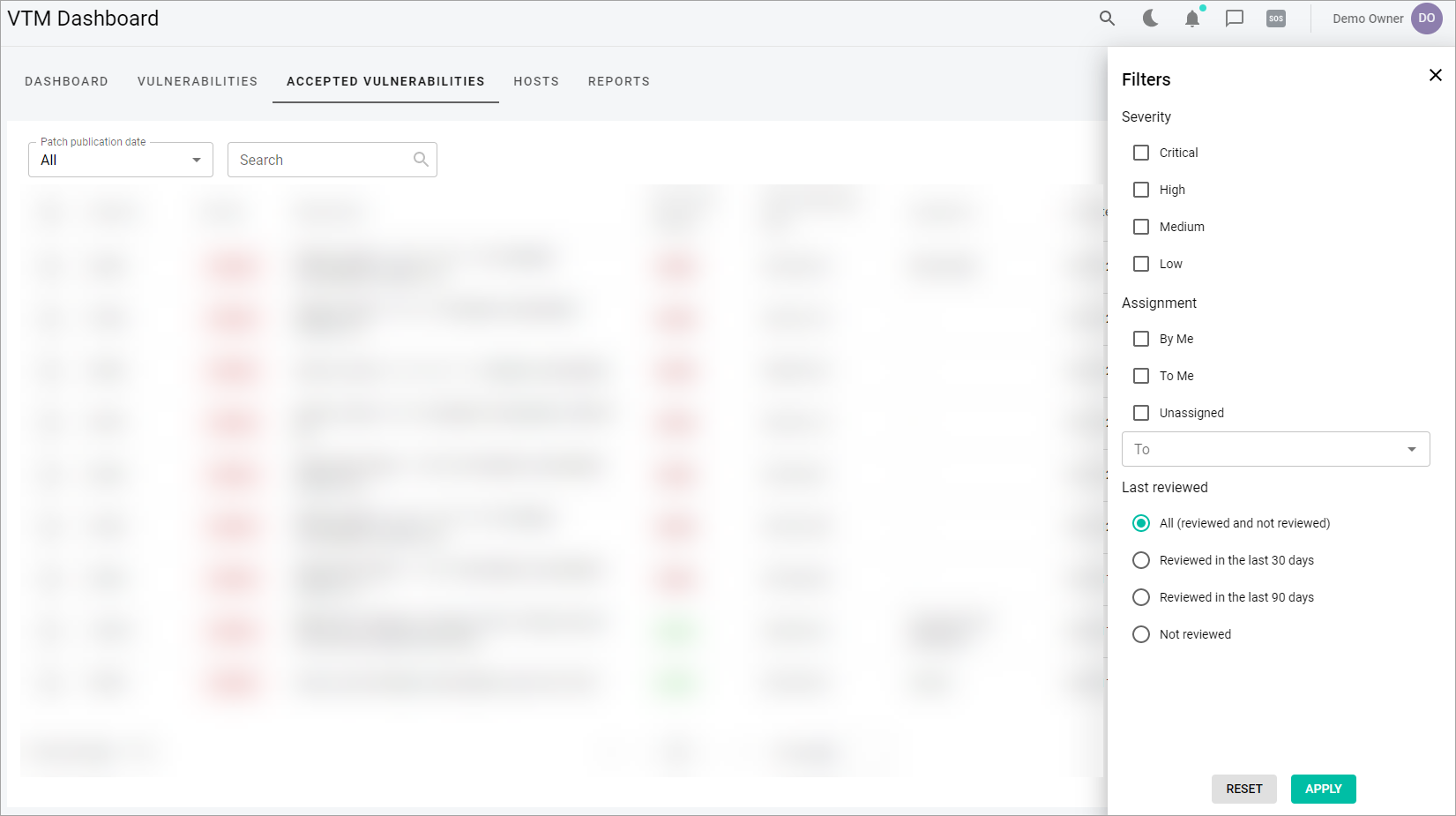
Accepted Vulnerabilities list can be filtered by the following criteria:
- Severity—shows accepted vulnerabilities with the selected severity status (Critical, High, Medium, Low) assigned.
- Assignment—shows accepted vulnerabilities assigned to another user by you (By me), to you by another user (To me), vulnerabilities that are not assigned (Unassigned), or vulnerabilities that are assigned to a particular user.
- To select a user, select the To dropdown list and then select the checkboxes near the needed users.
- Last reviewed—shows vulnerabilities that were reviewed within the selected date range (All, Last 30 Days, Last 90 Days, Not Reviewed)
To filter vulnerabilities list
- Select the Filter icon.
- In the Filters pop-up window, select the checkboxes near the needed options. You can select several filters at a time.
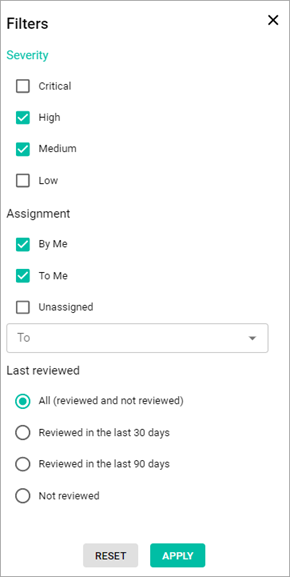
- Select the Apply button.
- To clear all filters, select the Clear Filters button that is now located next to the Search field.
Related Topics
Accepted Vulnerabilities Table
Search Accepted Vulnerabilities
View Accepted Vulnerability Details