Maturity
The Maturity metrics shows the overall maturity score and is broken down by control domain and category:
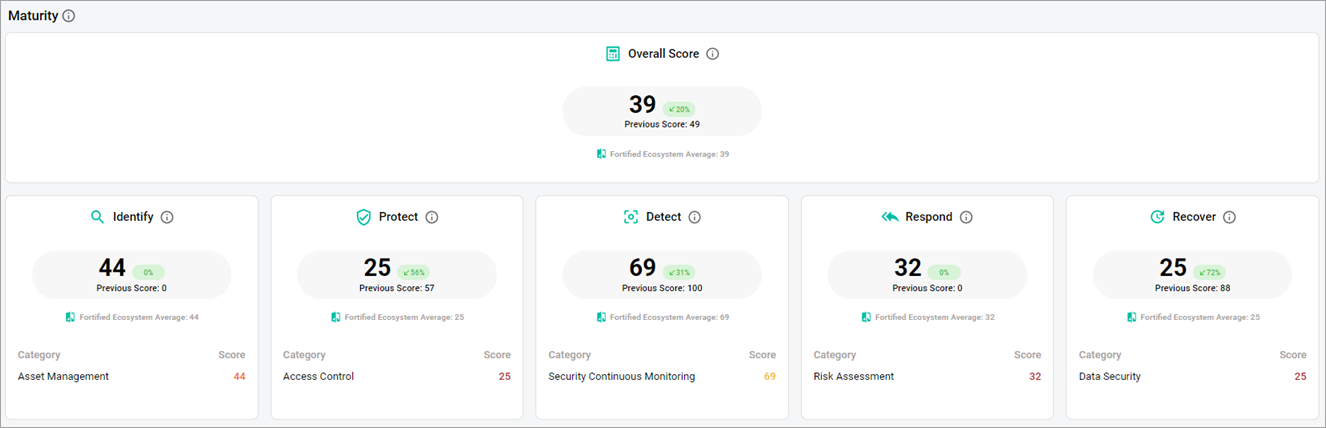
- Overall Score—this metric is the average of all control function scores from the most recent risk assessment along with a comparison of that score to the ecosystem average. If data from the previous assessment is available, a comparison to this score and the percentage of change will also be displayed.
- Govern— this metric establishes and monitors organization's cybersecurity risk management strategy, expectations, and policy. The outcomes of this Function inform an organization's overall cybersecurity risk management approach and activities.
- Identify—this metric is the average of all control category scores in the Identify function from the most recent risk assessment along with a comparison of that score to the ecosystem average. Individual category scores are provided for each category in the function (asset management, business environment, governance, risk assessment, risk management strategy, and supply chain risk management). If data from a previous assessment is available, a comparison to this score and the percentage of change will also be displayed. The Identify function refers to developing an organizational understanding of cybersecurity risk management for systems, people, assets, data, and capabilities.
- Protect—this metric is the average of all control category scores in the Protect function from the most recent risk assessment along with a comparison of that score to the ecosystem average. Individual category scores are provided for each category in the function (access control, awareness and training, data security, information protection process and procedures, maintenance, protective technology). If data from a previous assessment is available, a comparison to this score and the percentage of change will also be displayed. The Protect function refers to the development and implementation of appropriate protection measures to ensure the delivery of critical services.
- Detect—this metric is the average of all control category scores in the Detect function from the most recent risk assessment along with a comparison of that score to the ecosystem average. Individual category scores are provided for each category in the function (anomalies and events, security continuous monitoring, detection process). If data from a previous assessment is available, a comparison to this score and the percentage of change will also be displayed. The Detect function refers to the development and implementation of appropriate activities to identify the occurrence of a cybersecurity event.
- Respond—this metric is the average of all control category scores in the Respond function from the most recent risk assessment along with a comparison of that score to the ecosystem average. Individual category scores are provided for each category in the function (respond planning, communications, analysis, mitigation, improvements). If data from a previous assessment is available, a comparison to this score and the percentage of change will also be displayed. The Respond function refers to the development and implementation of appropriate activities regarding a detected cybersecurity incident.
- Recover—this metric is the average of all control category scores in the Recover function from the most recent risk assessment along with a comparison of that score to the ecosystem average. Individual category scores are provided for each category in the function (recovery planning, improvements, communications). If data from a previous assessment is available, a comparison to this score and the percentage of change will also be displayed. The Recover function refers to the development and implementation of appropriate activities to maintain resilience plans and restore capabilities or services that have been compromised due to a cybersecurity incident.
- Note: When you select a number, the system redirects you to the Assessment Worksheet Tab prefiltered by Function. When you select a category name, the system redirects you to the Assessment Worksheet Tab prefiltered by both Function and Category.
Related Topics